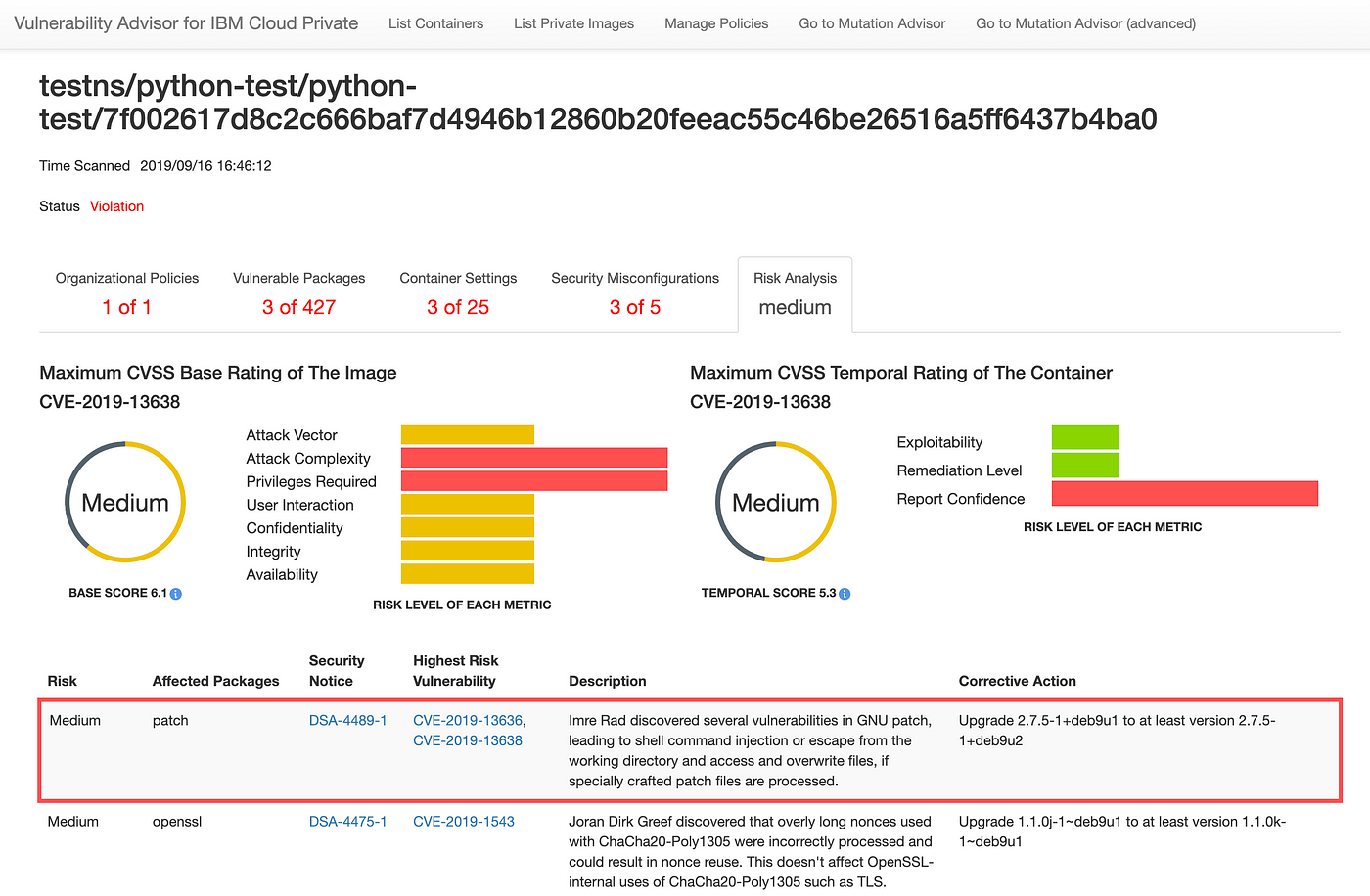
Assessing security risk of your containers with Vulnerability Advisor | by Yuji Watanabe | IBM Cloud | Medium

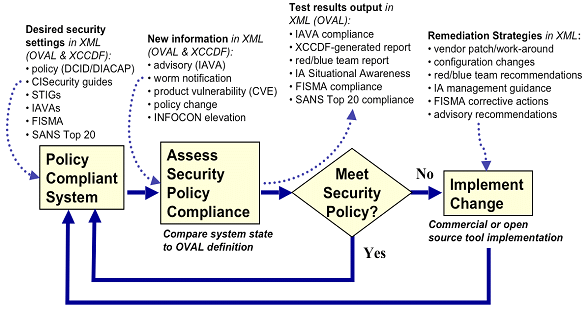
Figure 6 from Implementing a vulnerability management process GIAC ( GSEC ) Gold Certification | Semantic Scholar
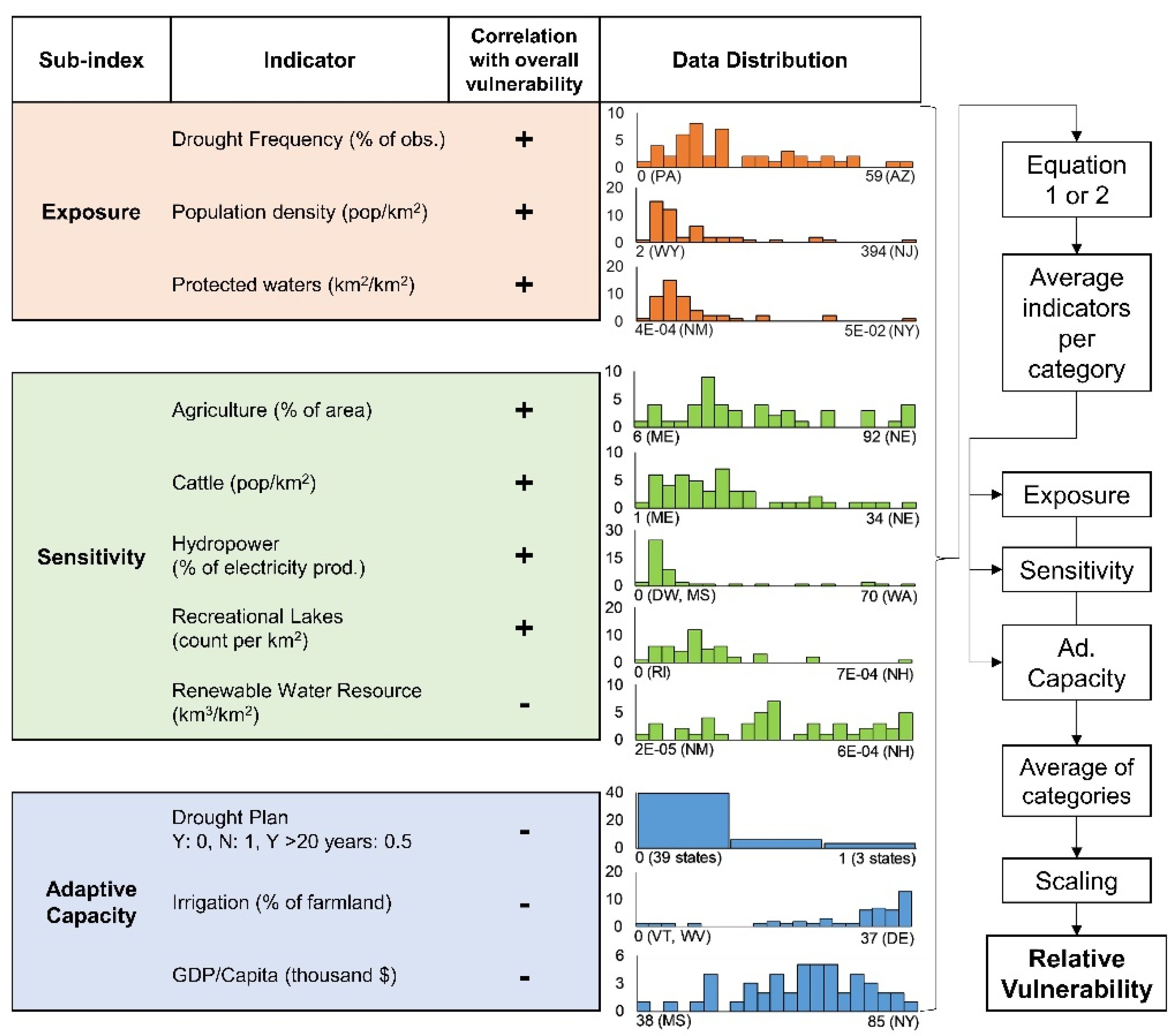
Water | Free Full-Text | Correction: Engström, J., et al. Drought Vulnerability in the United States: An Integrated Assessment. Water 2020, 12, 2033
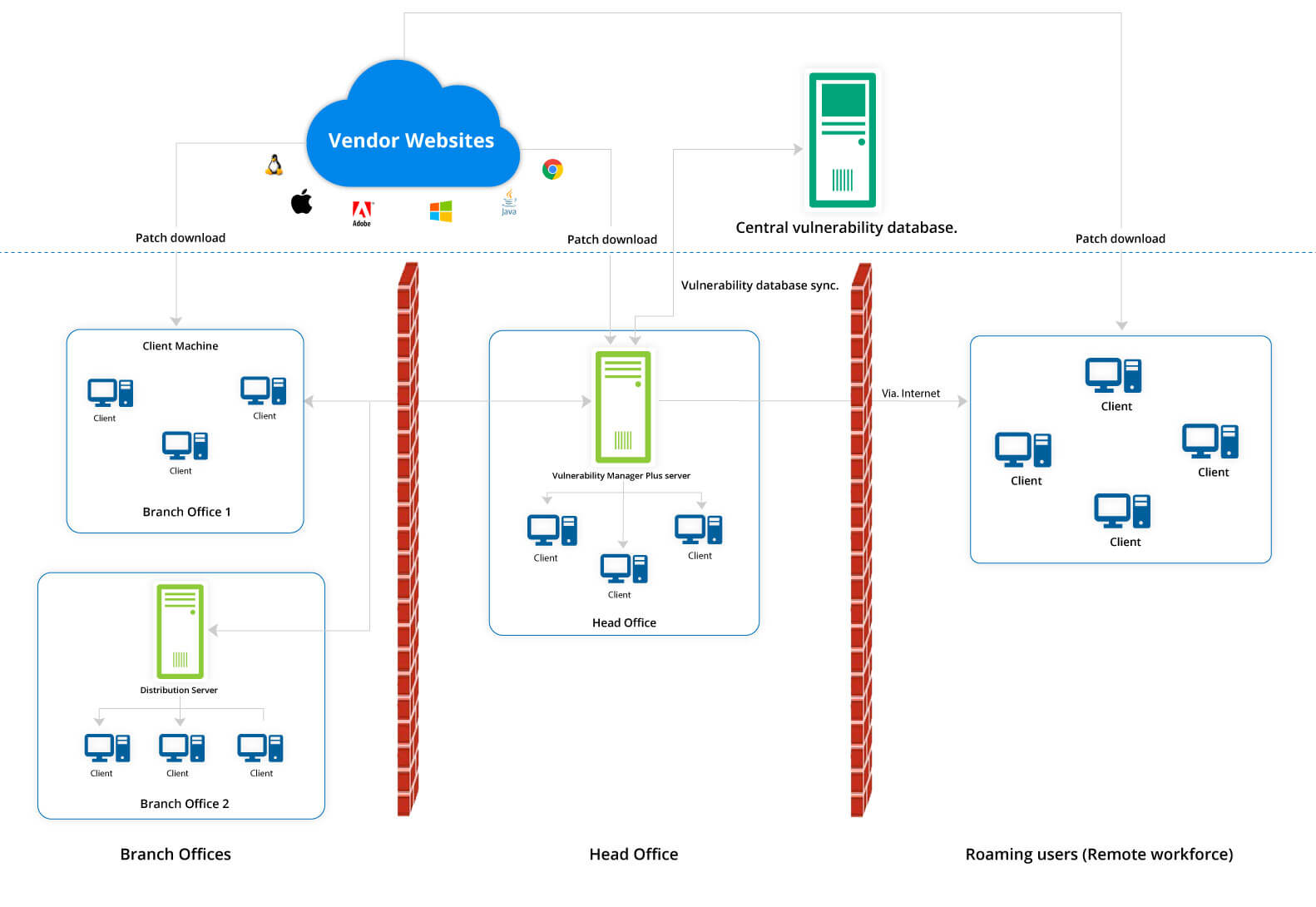
Définition de la gestion des vulnérabilités | Processus de gestion des vulnérabilités - ManageEngine Vulnerability Manager Plus

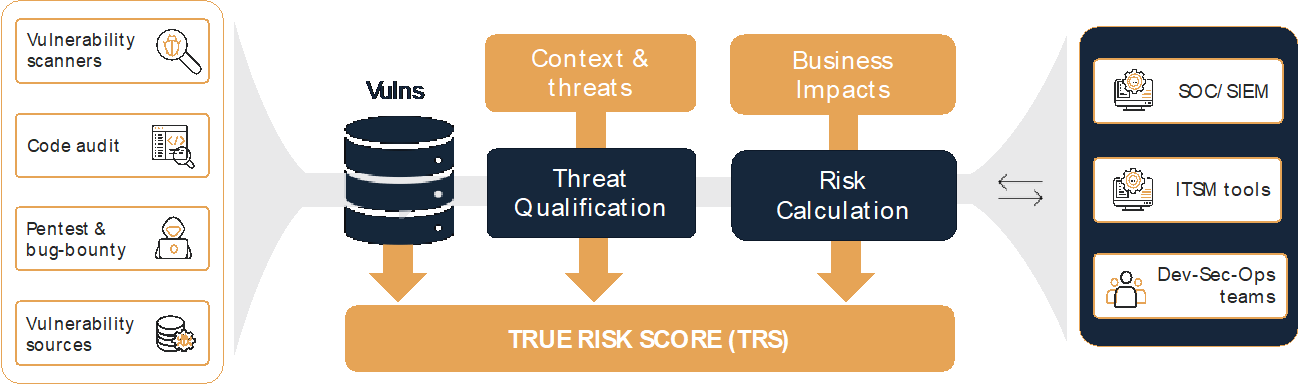
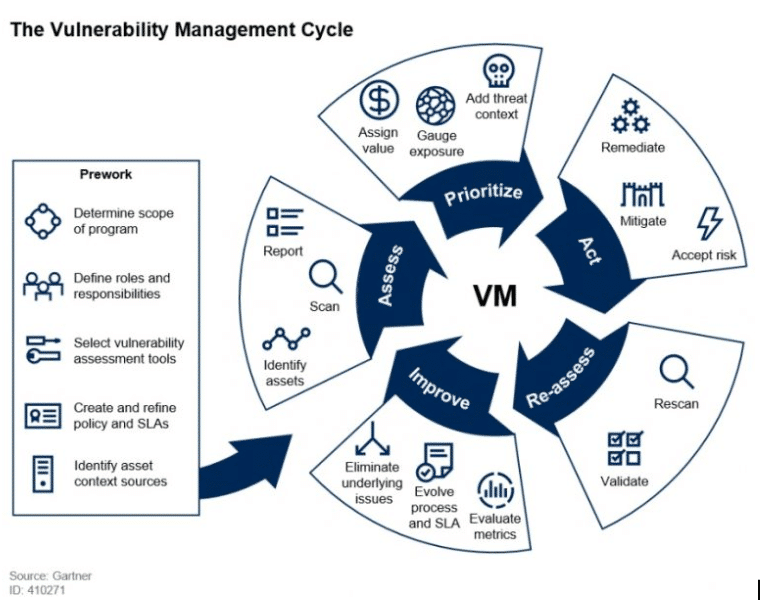
Managing vulnerabilities of information systems and information processing in enterprises – CISO practical point of view | TECH&DEV&SEC - technology, development & security